One of my Customers moving everything to Azure decided to replace internal Microsoft PKI with a managed solution from Digicert (Digicert bought Symantec certificate business recently).
At the present time Microsoft has an article describing Intune Configuration with Symantec PKI Manager Web Service: https://docs.microsoft.com/en-us/intune/certificates-symantec-configure
Unfortunately, it is not very clear what needs to be configured on Symantec (sorry, Digicert) side and I spent some time to get it working.
So, first of you need to talk to Digicert and get a Managed PKI environment.
After that, as per the article, generate a managed certificate and deploy your Managed PKI environment Root cert using Intune. It should be easy.
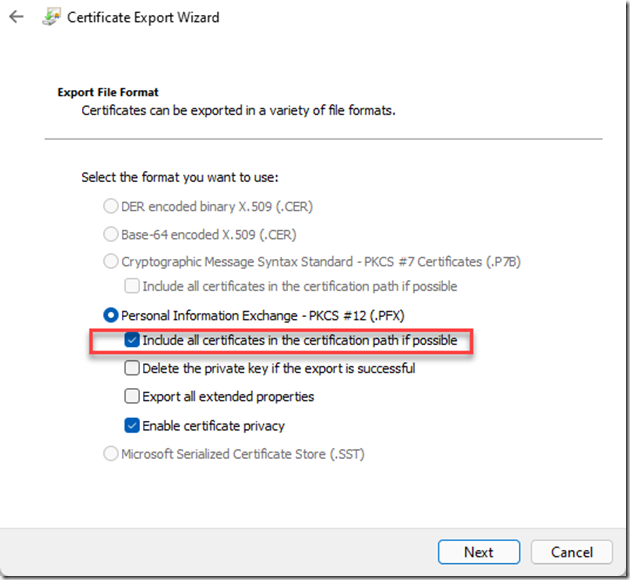
I took this certificate:


After that you need to add a certificate profile on Symantec side (MS article does not provide any details on it):

I select Client Authentication (User)

Give your template a friendly name, select a PKI Web Services as Enrollment method and click Advanced Options:

Now we need to do an interesting trick. It is in “Troubleshooting” section of Microsoft article and apparently is required if your UPN have a special characters. I need it even though my UPN did not have them… So:
– Click Add field and select Common Name (CN) and Webservice Request. That will create a new Common Name tab at the bottom. DO NOT click Save
– Delete the old Common Name (CN) at the top of the list.
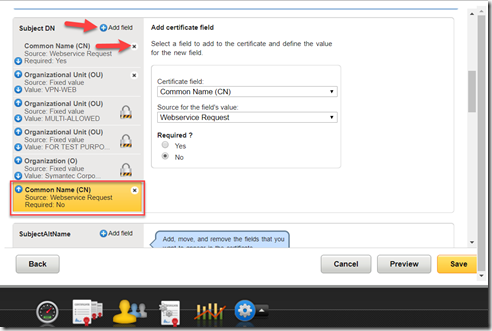
– You can customize other parameters. For example, I added an email as a Subject Alternative Name
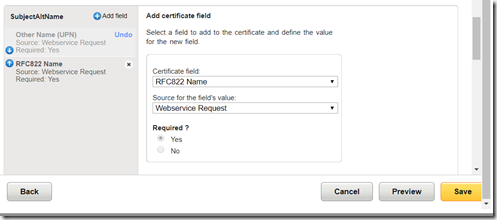
– Now you can save
Copy Certificate Template OID, you will need it for Intune:

At this point you can Download/Install Intune Connector. The procedure is described well in the Microsoft article.
When the connector is up:
you can create an Intune PKSC 10 profile (I also added EKU even though it is not in the doc):

Save the settings, click Create the profile and assign it to a group of users.
After Intune policy update the certificate should be requested by Intune on a Client behalf and deployed to your device: